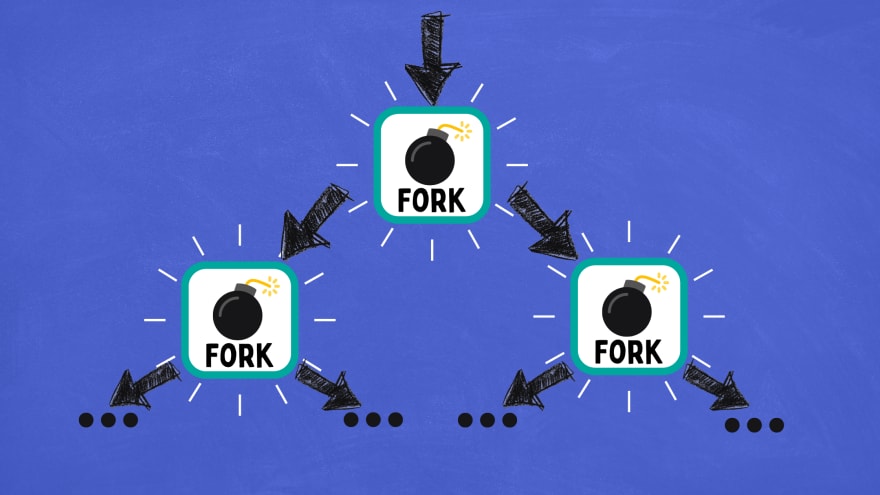
A fork bomb (also known as a rabbit virus) is a denial-of-service attack that consists of a process that constantly replicates itself to exhaust all available system resources, slowing down or crashing the system due to resource starvation.
Here's an example of the most popular fork bomb in Linux:
:(){ :|:& };:`
NOTE: do not run this on your system as it would crash the system!
Here's a quick rundown of all elements:
:()- Define the function. The:is the function name and the opening and closing parenthesis means that the function does not accept any arguments{ }- These characters show the beginning and end of the function:|:- Here it loads a copy of the function:into memory and pipe its own output to another copy of the:function, which has to be loaded into memory as well&- This starts the process as a background process:- The final:executes the function and hence the chain reaction begins
If you have a multi-user system, the best way to protect it against such attacks is to limit the number of processes a user can have by using PAM for example.
If you are already logged into the system you could do the following to stop the fork bomb:
- Run a SIGSTOP command to stop the processes of the user who ran the fork bomb:
killall -STOP -u someuser
For more information about the history of the fork bomb and other examples I would recommend checking this Wikipedia page: